Project Categories
Browse by type
-
IoT Projects
Arduino, ESP32, Sensors
-
Embedded Systems
Microcontrollers, Circuits
-
Web Applications
PHP, Laravel, React
-
Mobile Applications
Android, iOS, Flutter
-
AI & Machine Learning
Neural Networks, Deep Learning
Quick Links
Visit STS Shop
All Components In Stock
Arduino, Raspberry Pi, ESP32, Sensors, Motors & More!
Browse ComponentsReal Time Anomaly Detection for Network Traffic Patterns using Machine Learning
Need Components for This Project?
SoftTech Supply (STS) stocks all electronic components you need: Arduino boards, Raspberry Pi, ESP32, sensors, motors, displays, breadboards, and more.
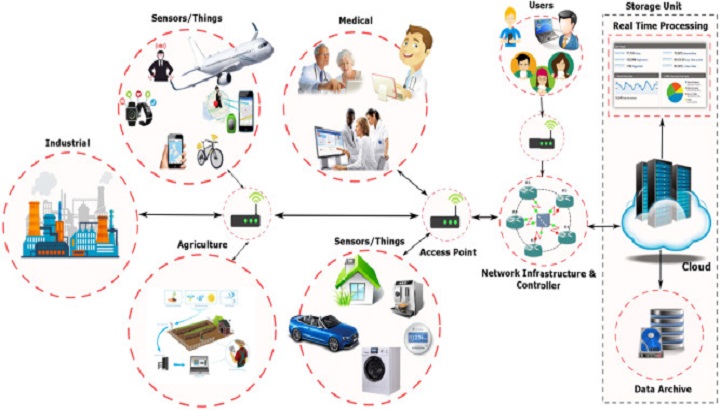
The client-side data generator simulates network traffic by generating data packets with various features, including packet size, source, destination, and timestamp. These data packets are sent to the server for real-time analysis. Additionally, the system supports integration with external sources of network data, such as ping statistics or network logs, enabling comprehensive anomaly detection.
The effectiveness of the system is evaluated through extensive testing using both simulated and real-world network data. Performance metrics, including detection accuracy, false positive rate, and response time, are measured to assess the system's reliability and efficiency. The results demonstrate the system's ability to accurately detect and respond to anomalies in real-time, enhancing network security and resilience against emerging threats.
Overall, the proposed real-time anomaly detection system offers a scalable and adaptive solution for safeguarding computer networks against malicious activities and unauthorized access, thereby ensuring the integrity and availability of critical network infrastructure.
Problem statements
- Processing Overhead: If the anomaly detection system requires significant computational resources, such as CPU or memory, it may introduce processing overhead. This overhead could potentially impact the performance of network devices or systems running the detection algorithms.
- Network Bandwidth: Transmitting and analyzing network traffic data for anomaly detection may consume additional network bandwidth. If the volume of data being analyzed is substantial, it could potentially saturate network links or cause congestion, leading to slower network speeds for other traffic.
- Slow Detection Times: Many systems take too long to detect network anomalies, leaving networks vulnerable to attacks.
- Too Many False Alarms: Existing anomaly detection systems generate too many false alarms, causing confusion and wasting resources.
- Complex Traffic Patterns: The intricate nature of modern network traffic makes it challenging to distinguish between normal and malicious activity.
- Need for Diverse Data Sources: Anomaly detection systems often overlook valuable data from different sources like network logs and application metrics.
- Difficulty in Understanding Alerts: Alerts from current systems are often hard to understand, making it challenging for analysts to respond effectively.
- Ineffective Security Measures: Current methods to protect computer networks are often unable to keep up with rapidly evolving cyber threats.
- Confusing Alerts: Security systems frequently generate alerts that are difficult to interpret, leading to delays in response and potential oversight of critical threats.
- Slow Response Times: Anomalies in network traffic are not detected promptly, leaving networks vulnerable to attacks and data breaches.
Ready to Build This Project?
STS Full Project Support
What We Provide:
- • All electronic components in stock
- • Step-by-step implementation guidance
- • Circuit design and wiring diagrams
- • Source code and programming support
- • Debugging and troubleshooting help
Why Choose STS:
- • Quality components at competitive prices
- • Fast delivery in Kigali and across Rwanda
- • Expert technical consultation
- • Complete documentation provided
- • Post-project support available
More Project Ideas from STS
AI-Based Smart Security System
Security systems are essential for homes, offices, and industries, but traditional systems often rely on simple motion detection, which can generate false alarms. This project implements an AI-based intruder detection system using computer vision and deep learning. The system uses YOLO or OpenCV...
AI-Powered Smart Farming System
This project integrates soil moisture sensors, temperature sensors, and weather forecasting data to create an intelligent farming assistant. AI algorithms analyze the soil's moisture content and predict the best irrigation schedule, reducing wate...
AI-Based Health Monitoring System
This project involves designing a wearable health monitoring system that continuously tracks heart rate, body temperature, blood oxygen levels (SpO2), and other vital signs using sensors like MAX30100, DS18B20, and DHT11. The collected data is processed using machine learning algorithms to identi...
AI-Powered Smart Traffic Management System
Traffic congestion is one of the biggest challenges in modern cities, causing delays, pollution, and inefficient fuel consumption. This project leverages computer vision and deep learning to analyze real-time traffic footage from CCTV cameras. The...
About This Project at SoftTech Supply
This Real Time Anomaly Detection for Network Traffic Patterns using Machine Learning project can be implemented using components available at SoftTech Supply (STS) in Kigali, Rwanda. Whether you need Arduino boards, Raspberry Pi, ESP32, ESP8266, sensors, microcontrollers, or any other electronic components, we have everything in stock. STS provides complete project support including component selection, circuit design, programming assistance, and troubleshooting. Our team can help you implement this project from start to finish. Visit our electronics shop or contact us for personalized consultation. We serve students, hobbyists, and professionals across Rwanda with quality components and expert technical support.